It’s been a while since I last analyzed malware. While I don’t consider myself an expert, I still enjoy reviewing potentially malicious files to identify what they are and determine their intent. Over the weekend, I came across a post on Reddit that grabbed my attention, so I spun up my REMnux VM and decided to take a closer look.
When analyzing malware, it’s always important to use an isolated machine. Never your host system. REMnux is my go to because most malware is designed to target Windows, so the likelihood of accidentally infecting my Linux-based analysis environment is relatively low. One thing to keep in mind is that some malicious websites fingerprint the GET request used to download a payload. If the request doesn’t come from a specific environment or browser, they may redirect to a benign page instead. Fortunately, that wasn’t the case here and I was able to successfully retrieve the file for analysis.
REMnux also comes with a solid suite of built-in tools for malware analysis. I often use it when examining malicious emails, Word or Excel documents, leveraging tools like oletools, ViperMonkey, or emldump. For executable files, my typical workflow starts with DIE (Detect It Easy) to inspect the file structure, followed by FLOSS or strings and finally running some Yara rules against it.
The domain in question is combatshell[.]com. At first look, it appears legitimate and it’s styled to resemble a game site, complete with a “Beta Launcher” tab. However, this tab links to combatshell[.]com/downloader/combatshell.zip, which hosts malware disguised as a game installer.
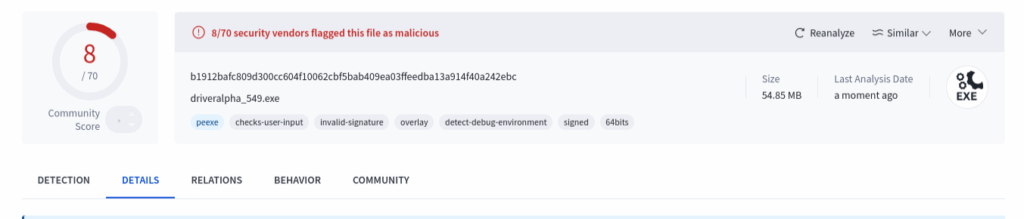
The full ZIP URL currently shows a 0/97 score on VirusTotal. However, once extracted, the actual executable within the ZIP does trigger several detections. As always, remember to hit the “reanalyze“ button when reviewing files on VirusTotal as it had a clean 0/70 score until I rescanned which produced the below results.
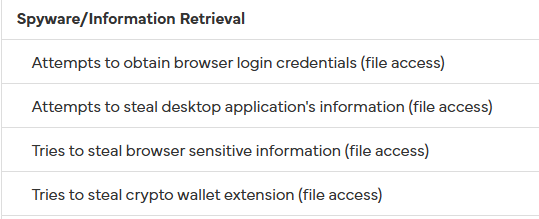
While VirusTotal results provide some indication that the file is malicious, I wanted to better understand what it actually does. My next step was to execute the malware in a virtualized environment and observe its behavior. For dynamic analysis, my go-to platforms are tria.ge and Hybrid Analysis. You can view the report from Hybrid-Analysis here.
Based on the analysis results, it’s clear that this binary functions as an information and cryptocurrency stealer. It attempts to harvest browser login credentials and access locally stored crypto wallets. To maintain long-term access, it establishes persistence by dropping a file into the user’s startup directory, ensuring it executes on each system reboot. Additionally, it makes a request to the legitimate service api.ipify.org to retrieve the victim’s public IP address, likely used to fingerprint and catalog its victims.

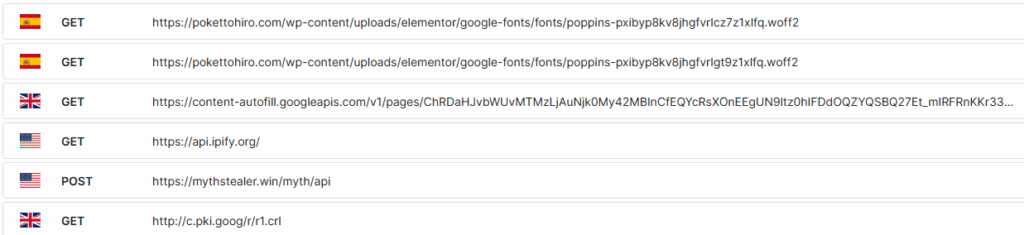
What stood out most during the analysis was the POST made to an external web server. In networking, a POST request is used to send data from a client to a server, and in this case, the malware is clearly exfiltrating sensitive information as described below.
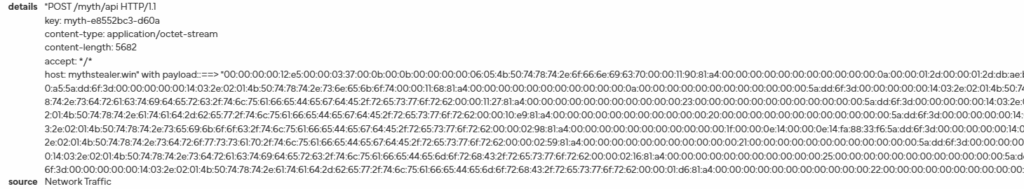
The payload appeared to be in Hex, and after entering it into CyberChef and cleaning it up, I confirmed my suspicion. Using the ‘From Hex’ recipe, the output was as follows:
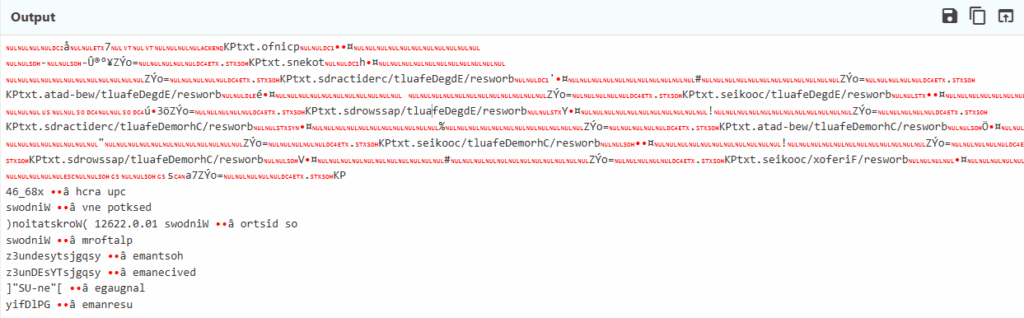
I copied and pasted the content into ChatGPT and had it reverse some of the output. For instance, ‘KPtxt.sdractiderc/tluafeDegdE/resworb’ was transformed into ‘KPtxt.directory/filedEdge/browser’. Below is the full output. It’s evident that the malware is functioning as an information stealer, exfiltrating data from popular browsers like Edge, Chrome, and Firefox, along with some system related information.
KPtxt.pincfo
KPtxt.token
KPtxt.directory/filedEdge/browser
KPtxt.data-back/filedEdge/browser
KPtxt.cookies/filedEdge/browser
KPtxt.passwords/filedEdge/browser
KPtxt.directory/filedChrome/browser
KPtxt.data-back/filedChrome/browser
KPtxt.cookies/filedChrome/browser
KPtxt.passwords/filedChrome/browser
KPtxt.cookies/Firefox/browser
Data:
- 6543757952 ESLAF
- 12622.0.01 Windows '†â even desktop
- z3undesytsjgqsy '†â hostname
- z3unDEsYTsjgqsy '†â device name
- "SU-ne" '†â language
- yifDlPG '†â username
- 261.21.421.46 '†â IP address
References:
- KPtxt.pincfo
- KPtxt.token
- KPtxt.directory/filedEdge/browser
- KPtxt.data-back/filedEdge/browser
- KPtxt.cookies/filedEdge/browser
Encrypted Values:
- WCzSgBA8LuvobpckD4seNyD7BgrGHHQA=gis:2=v:1666611271=t:1620801271=i:1=x:1=u:
- s9tkvmzrywR5JqpHNwBUBEVd3c2
Entries:
- 6543757952 ESLAF / TRUE
- m3e7-5zyFdgyt49xr
- .oYQJhRvIwE1hssbLBBzC05-MW1tzoGGkpBve-A6HAVBzydpB9vcn2teHcTgB9I_-YXkdmxJMxlH
- content_Adobe
- 960643707132%UtmLkJD2%6712639899667425
IP Addresses:
- 261.21.421.46
- z3unDEsYTsjgqsyI was also surprised by how blatantly obvious the attacker left the domain by using mythstealer[.]win, which made attribution straightforward. It was recently registered on 6/21 and the domain name also allowed me to quickly confirm the malware family, making my analysis significantly easier. A quick Google search confirms this, identifying it as a well-known info-stealer written in Rust, specifically designed to target gamers and cryptocurrency users. For further details, Trellix provides a more in-depth review on its capabilities.

Using the strings utility in REMnux, I found multiple references to Rust libraries throughout the binary, which further strengthens my suspicion that it’s associated with Myth Stealer.
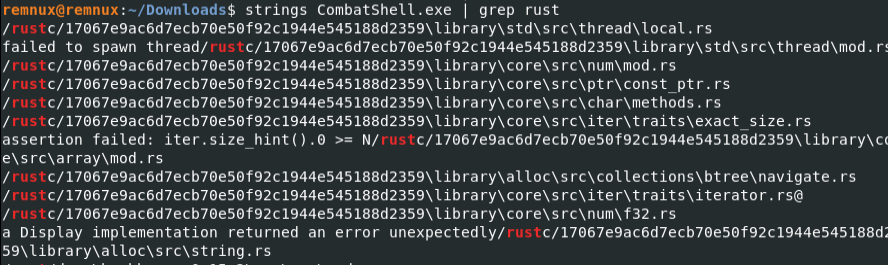
Based on my analysis and the supporting details in the attached Trellix article which outlines the initial access methods and behavioral indicators, I strongly believe this malware is Myth Stealer. This conclusion is supported by the following observations, which closely align with the traits documented in the Trellix report:
- The Command and Control (C2) domain used is mythstealer[.]win matches the name Mythic.
- The malware is distributed via fake gaming websites, often branded with a “Beta” suffix.
- The malware is built with Rust as observed using Strings command.
- It uses api.ipify.org to retrieve the victim’s public IP address.
- It establishes persistence by creating a file named mcr.lnkk in the Windows Startup folder.
- Dynamic analysis in Hybrid Analysis shows clear signs of information-stealing behavior.
- The malware demonstrates sandbox evasion techniques to avoid detection during analysis.
This post just scratches the surface of malware analysis, and what is expected of SOC analysts. You could go further by conducting analysis on a machine like FlareVM, which is a Windows VM with built in tools for malware analysis. We could also check the APIs used by the file against malapi.io. For example, SleepEx seen in the strings is used to suspend execution of thread for a set amount of time, and is used for time based evasion.
To protect against these types of attacks, defense in depth is essential. Organizations should implement multiple layers of security, including:
- Limit user privileges: Ensure users do not have administrative access unless absolutely necessary.
- Trusted sources only: Encourage users to download files exclusively from known, trusted locations such as the company’s internal portal.
- URL and DNS filtering: Use filtering solutions to block access to malicious or suspicious websites.
- Endpoint protection: Deploy antivirus or Endpoint Detection and Response (EDR) solutions on all endpoints, with Security Operations Center (SOC) analysts actively monitoring and ready to respond to any detected threats.
- Network monitoring: Implement Network Detection and Response (NDR) or open source solutions like Suricata to monitor network traffic for suspicious or malicious activity.
This layered approach significantly reduces the risk and impact of malware infections.
Indicators of Compromise (IOCs):
- MythStealer Sample: b1912bafc809d300cc604f10062cbf5bab409ea03ffeedba13a914f40a242ebc
- Downloader Domain: combatshell[.]com
- C2 Domain: mythstealer[.]win
- C2 IP Address: 172.67.182.176
