As someone working in cybersecurity, I find blog posts like this recent one from The DFIR Report to be incredibly valuable. They provide insight into attacker tradecraft and mindset, while also presenting opportunities to enhance our own detection and prevention capabilities.
I regularly review these kinds of reports and evaluate how the described tactics, techniques, and procedures (TTPs) compare to what’s currently deployed in my environment. Attackers are constantly evolving their methods to gain initial access and achieve their objectives. When I first started in cybersecurity, Word and Excel files with malicious macros were and still are commonly used as initial access vectors. Over time, attackers transitioned to using ISO and VHD files to bypass Mark-of-the-Web protections. More recently, we’ve seen the emergence of “Click to Fix” attacks.
As adversaries continue to evolve their techniques, it’s critical that we, as defenders, also adapt and innovate our defenses to stay ahead of emerging threats. Implementing proactive, actionable controls can significantly reduce risk. For example, disabling macros in Microsoft Office documents, blocking the mounting of ISO/VHD files, or restricting user access to the Win+R hotkey are practical defensive measures that can help prevent the types of attacks highlighted above.
Below are several high-level observations from the recent DFIR report, along with what I, as a defender, would implement or investigate to detect or prevent these behaviors:
- Exposed RDP in 2024?
The attack occurred in 2024, yet RDP was still exposed to the internet without basic protections in place. At a minimum, RDP should be protected with multi-factor authentication (MFA) or IP allowlisting. That said, exposing RDP even with these controls presents risk. A VPN would be more appropriate, offering defenders better visibility and control. - Administrative Account Used for Remote Access
The attacker used an administrator account to log in remotely. Organizations should restrict remote access for privileged accounts and instead enforce that only standard user accounts are used for remote connectivity. - Unrenamed Hacking Tools
Tools like Mimikatz, CredentialsFileView, Advanced IP Scanner, and Netscan were executed without being renamed or obfuscated. These should have triggered multiple detections in a properly tuned SOC and warranted immediate investigation. - Suspicious Network Scans
Any device performing network scans, especially systems not typically used for such activity like vulnerability scanners should raise red flags and be investigated promptly. - Abuse of Remote Management Tools
Yet again, we see abuse of legitimate remote management (RMM) tools. Organizations should maintain a known-good list of approved RMM software and block all others using allowlisting or EDR controls. Here’s a useful reference to help identify common RMM tools that may be misused. - DCSync From a Non-Domain Controller
A DCSync attack initiated from a non-domain controller should immediately trigger alerts. This is a high-risk behavior indicative of credential theft attempts targeting Active Directory. - Living-off-the-Land (LOTL) Techniques
The attacker used built-in utilities like net, ipconfig, and nltest for reconnaissance are classic LOTL techniques. These tools should be monitored for use within a short time frame or correlated with user and device behavior to flag anomalies, especially since typical end users should not be running them under normal circumstances. - Outbound Exfiltration Over SSH (Port 443) and SMB
Data was exfiltrated over SSH on port 443 designed to evade traditional port-based firewall rules. Preventing this requires application-aware firewalls (e.g., Palo Alto, Fortinet) capable of inspecting traffic beyond port numbers. Outbound SMB should also be blocked unless explicitly required.
Time to Ransomware: 118 Hours
This attack was noisy, and any capable SOC should have been able to detect and contain it well before the ransomware was deployed. The adversary connected from known malicious IPs, used off-the-shelf tools without renaming them, and installed unauthorized remote access tools for persistence. These are all highly detectable behaviors.
One key lesson from reports like this is understanding how and when to respond. The concept of the “Strike Zone“, a term coined by Mandiant highlights the importance of timing. Respond too early, and the attacker may detect your response and accelerate their actions. Respond too late, and they may already have achieved their objectives, such as exfiltrating data or deploying ransomware.
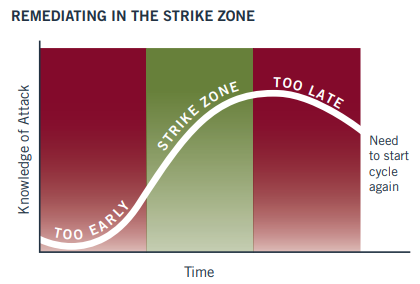
In this case, if the organization had disabled RDP access after the attacker had established persistence through RMM tools, the attacker could have simply used those tools to regain access and inflict further damage. A well-coordinated response by disabling RDP, deactivating accounts, and removing persistence mechanisms simultaneously would have been required to effectively remove the threat without tipping off the attacker prematurely.
A final note: Organizations without a mature cybersecurity program should consider adopting a framework like the CIS Critical Security Controls (CIS Top 18) to assess their environment and begin implementing appropriate safeguards. These controls provide a prioritized, actionable roadmap to help organizations detect, respond to, and ultimately prevent the types of attacks outlined in reports like this. Starting with foundational controls can make a significant difference in reducing risk and improving overall security posture.
